A regular day in a manufacturing setup looks much similar to the “Beer Game” by MIT Professor Jay Forrestor in the year 1960, and discussed in detail by Peter Senge in his seminal book The Fifth Discipline to ...
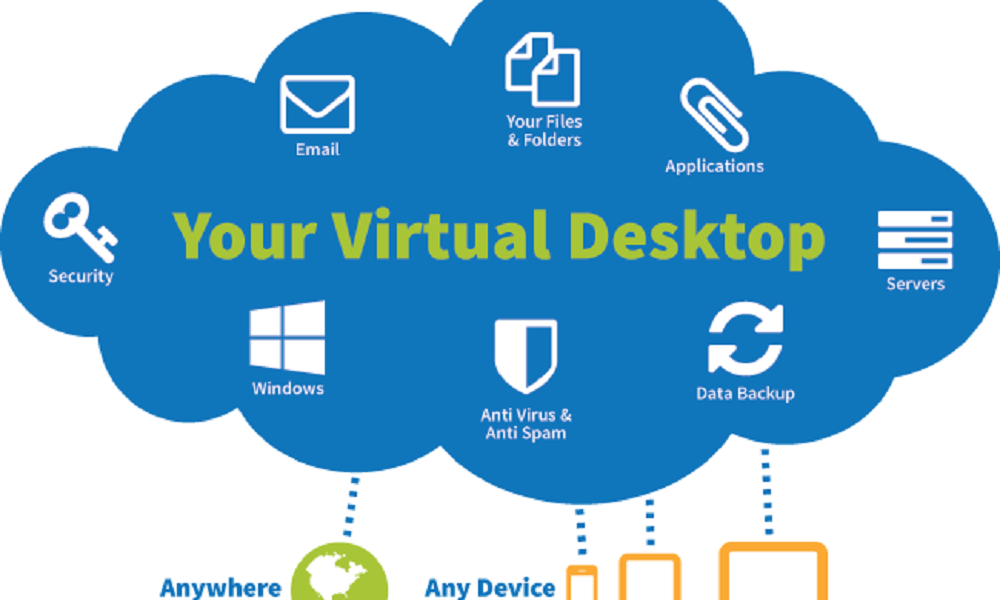
A technology which started almost 15 years back seems to finds its mojo back during these times. My discussion with few key stakeholders and clients broadly directs me to following two reasons ; a) Dig...
Data protection is a mess, be it your organization or any other. We have our sensitive data scattered across laptops, mobile, DC & DRs, multiple clouds and across hundreds of applications. More often than n...
Download E-book Cyber security is something that is constantly on our mind here at Unit. This is because, according to Bloomberg, cyber security related issues costs companies around $400 Billion a year on aver...
In a recent Indeed survey of more than 1,000 hiring managers and recruiters, more than half (53 percent) of respondents have hired tech talent despite candidates not meeting the job description requirements. Th...
Small and medium-sized businesses (SMB) have to juggle many priorities and daily demands. Acquiring and retaining customers. Avoiding inefficiency. Delivering excellent customer service. Managing costs. Hiring ...
Computer and network security: Everyone knows they should be doing it better, but no one really knows all the best ways to do it. The computer security profession is a large and varied one, so — obviously — opi...